When Updates Go Wrong: What the CrowdStrike Incident Teaches Us
We’ve all been there—you’re working, and suddenly, your apps or tools stop working. Recently, this …

As per Wikipedia, the term data breach refers to compromise of security involving unauthorized access to sensitive and confidential user information.

KPMG Survey - A triple threat across the Americas
A recent survey by KPMG confirms the threat of fraud, cyber -attacks and compliance. 600+ senior leadership from seven industries across Latin and North America participated in the survey.
9 in 10 respondents say that remote working has reduced their ability to monitor behavior, thereby increasing the risks of external/internal fraud. 31% respondents also confirmed fraud perpetrated by an insider in the past year.
Respondents also agreed that compliance has now become a reputational issue for enterprises. On an average, it takes about a month to fully contain a cyber-attack. there is a potentially fatal lack of urgency for most companies across the globe. not enough companies have championed fraud controls, compliance, and cybersecurity. it is also agreed that fraud, non-compliance, and cyber breaches cost dearly to the organization.
5 Facts About Data Breaches
Data breaches have increased over the recent years and affected enterprises of all sizes. The resultant damage of these data breaches costs several millions of dollars. For instance, T-mobile data breach cost $350 million. Hence, organizations should focus more on securing their networks; staff should have strong passwords and employees must be trained to identify the red flags.

We’ve all been there—you’re working, and suddenly, your apps or tools stop working. Recently, this …

In programming, the concept of a one-size-fits-all language is a fallacy. Different languages offer …
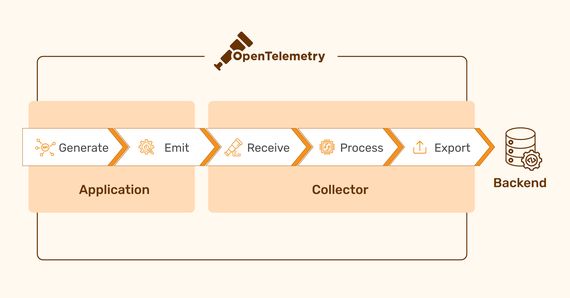
Modern software development often leverages distributed architectures to achieve faster development cycles …
Finding the right talent is pain. More so, keeping up with concepts, culture, technology and tools. We all have been there. Our AI-based automated solutions helps eliminate these issues, making your teams lives easy.
Contact Us